Is blockchain really secure? Here are four pressing cyber threats you must consider

Blockchain will be key to embracing the Fourth Industrial Revolution, be we must be wary of cyber threats. Image: Unsplash/Adi Goldstein
Yazeed Alabdulkarim
Principal Research and Innovation Advisor, Saudi Information Technology Company (SITE)Listen to the article
- Blockchain is a key technology of the Fourth Industrial Revolution, creating new innovative opportunities and disrupting existing systems.
- Decentralized digital transformation is achieved by creating trust between parties and eliminating intermediaries, thus facilitating easy data sharing.
- But while blockchain uses security primitives such as cryptography, extra efforts must be made to secure its architecture and mitigate threats.
Blockchain is a key technology of the Fourth Industrial Revolution, blurring the lines between physical and digital spaces. It creates new innovative opportunities and disrupts existing businesses by enabling decentralized digital transformation.
This decentralization is achieved by creating trust between parties and eliminating intermediaries, to facilitate efficient data sharing and value exchange.
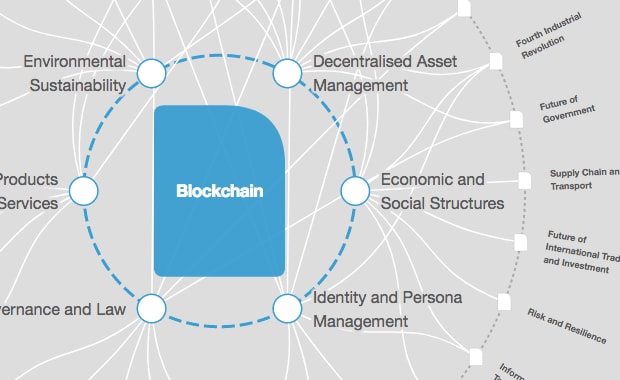
Blockchain is commonly associated with bitcoin and other cryptocurrencies, but its use cases go beyond financial applications to include various business domains such as agriculture, mining, manufacturing, energy, supply chains and healthcare.
However, while blockchain technology utilizes security primitives, such as cryptography, additional efforts must be made to secure its large-scale architecture and mitigate cyber threats.
The potential of blockchain technology
With 61% of companies ranking digital transformation as a top priority, blockchain is becoming an essential technology in achieving that objective by providing means of sharing data and exchanging value securely between organizations.
Blockchain use cases are expanding due to its unique set of features, with its global market size expected to reach US$1.43 trillion by 2030, with a compound annual growth rate (CAGR) of 85.9%.
Blockchain is mainly used to facilitate information sharing and value exchange between parties, which can be utilized for various domains (see below).

One such successful application is using blockchain to improve the efficiency of supply chains by tracking goods in a transparent and timely manner.
Blockchain also enables the creation of new business models and approaches laying the ground for Web3 applications. For instance, creating decentralized platforms for social networking, content management, marketplaces and so on.
The technology can be further used to create new digital assets, such as carbon assets, or represent physical ones, such as real estate and gold.
Why prioritize cybersecurity in blockchain?
Despite the great opportunities of using blockchain technology in businesses, it does also have its adverse effects.
For example, cryptocurrencies are used as methods of payment in criminal activities, such as ransomware, scams, and terrorism financing, reaching a value of $14 billion in 2021, a 79% increase compared to 2020.
Moreover, blockchain technology introduces new cybersecurity threats with unique security challenges. Consequently, cybersecurity should be one of the most critical elements to accepting and using blockchain.
Since blockchain is built upon established cryptographic technologies, it is commonly misinterpreted as a secure by design technology. But these inherited cryptography features are insufficient to withstand all cybersecurity threats.
A group of researchers has identified about 500 cybersecurity attacks, considering cryptocurrencies only, with losses reaching $9 billion. Protection against these attacks is challenging mainly due to blockchain’s decentralization and openness.
These characteristics increase the complexity of operations and reduce the ability to gain complete control, calling for a thorough assessment to protect against cybersecurity threats and associated vulnerabilities.
Four main cybersecurity threats to consider
Blockchains have large-scale architecture with many layers, such as consensus, smart contracts, networks and endpoint clients. These layers are often targeted in cyber-attacks , exposing a wide variety of vulnerabilities.
We highlight four major cyber threats that need to be considered with regards to blockchain. These are:
1. Consensus protocol threats
Blockchains use consensus protocols to reach agreement among participants when adding a new block. Since there is no central authority, consensus protocol vulnerabilities threaten to control a blockchain network and dictate its consensus decisions from various attack vectors, such as the majority (51%) and selfish mining attacks.
Consequently, the consensus protocol must be evaluated and tested properly to ensure it always reaches an expected resolution.
2. Breach of privacy and confidentiality
The second threat is related to the exposure of sensitive and private data. Blockchains are transparent by design, and participants may share data that attackers can use to infer confidential or sensitive information.
As a result, organizations must carefully evaluate their blockchain usage to ensure that only permitted data is shared without exposing any private or sensitive information.
3. Compromising of private keys
The third threat is the compromising of private keys that blockchains use to identify and authenticate participants.
Attackers may compromise private keys to control participants’ accounts and associated assets by using classical information technology methods, such as phishing and dictionary attacks, or by exploiting vulnerabilities in blockchain clients’ software.
For example, the January 2017 attack on the Coincheck cryptocurrency exchange led hackers to steal about $500 million from customers’ wallets due to weak security controls.
4. Smart contract defects
The fourth threat is that of smart contract defects that adversaries may exploit to launch attacks.
An attacker exploited a smart contract vulnerability in 2016 to steal about $60 million from blockchain crowdfunding platform, the Decentralized Autonomous Organization (DAO).
Thus, smart contracts must be evaluated and appropriately tested to resolve possible defects and adhere to business and legal requirements.
Key actions for blockchain security
To improve blockchain security, we recommend the following three actions:
Provide education and training and adopt industry best practices such as Gartner's Blockchain Security Model when planning to implement blockchain technology to mitigate its risks. Implement sensible regulations of blockchain and expand them globally to increase adoption and build trust of the technology.
Implement a cybersecurity assessment process for blockchain solutions that follows secure software development practices to address related cybersecurity threats, mitigate risks, and provide continuous monitoring to new threats and incidents.

A proposed process, as outlined in diagram above, begins by defining security objectives that align with current business continuity, crisis management and security policies. The evaluated blockchain solution must be configured to meet these objectives.
Next, stakeholders should perform a risk assessment to discover potential threats and existing vulnerabilities. This assessment may be conducted following the same framework used by organizations for other information technology deployments.
Organizations must then create security controls and associated governance protocols to reduce the identified risks. If software development is required, organizations must develop the requirements following secure development practices, such as the secure software development life cycle (S-SDLC) methodology.
Finally, organizations must continuously monitor and audit security in response to new threats and incidents.
How is the World Economic Forum promoting the responsible use of blockchain?
Emerging technologies are bringing great opportunities that must be seized early on. On the other side of the spectrum, there are always malicious actors who are trying to exploit these technologies before reaching maturity to discover new cyber threats and cause harm.
Blockchain is one of these technologies, so wear your cyber safeguards before embracing it and beware of the other side of the spectrum.
Don't miss any update on this topic
Create a free account and access your personalized content collection with our latest publications and analyses.
License and Republishing
World Economic Forum articles may be republished in accordance with the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License, and in accordance with our Terms of Use.
The views expressed in this article are those of the author alone and not the World Economic Forum.
Stay up to date:
Blockchain
Related topics:
Forum Stories newsletter
Bringing you weekly curated insights and analysis on the global issues that matter.