Quantum-safe migration: Why now is an opportunity to modernize cryptography for the new age

The quantum-safe migration is complex but essential for business resiliency Image: Getty Images/iStockphoto
- The rise of quantum computing introduces systemic risks to cybersecurity but also creates the opportunity to elevate cryptography as a strategic asset that enhances business resilience.
- Three practices – cryptographic inventory, cryptographic agility and cryptographic defence-in-depth – underpin a resilient cryptographic framework.
- To thrive amid uncertainty, organizations should proactively harness emerging technologies, make informed choices and manage cryptography with long-term resilience and risk management in mind.
As quantum computing advances, it brings unprecedented opportunities as well as significant threats. One major concern is that it could break the cryptographic systems that underpin our digital trust today.
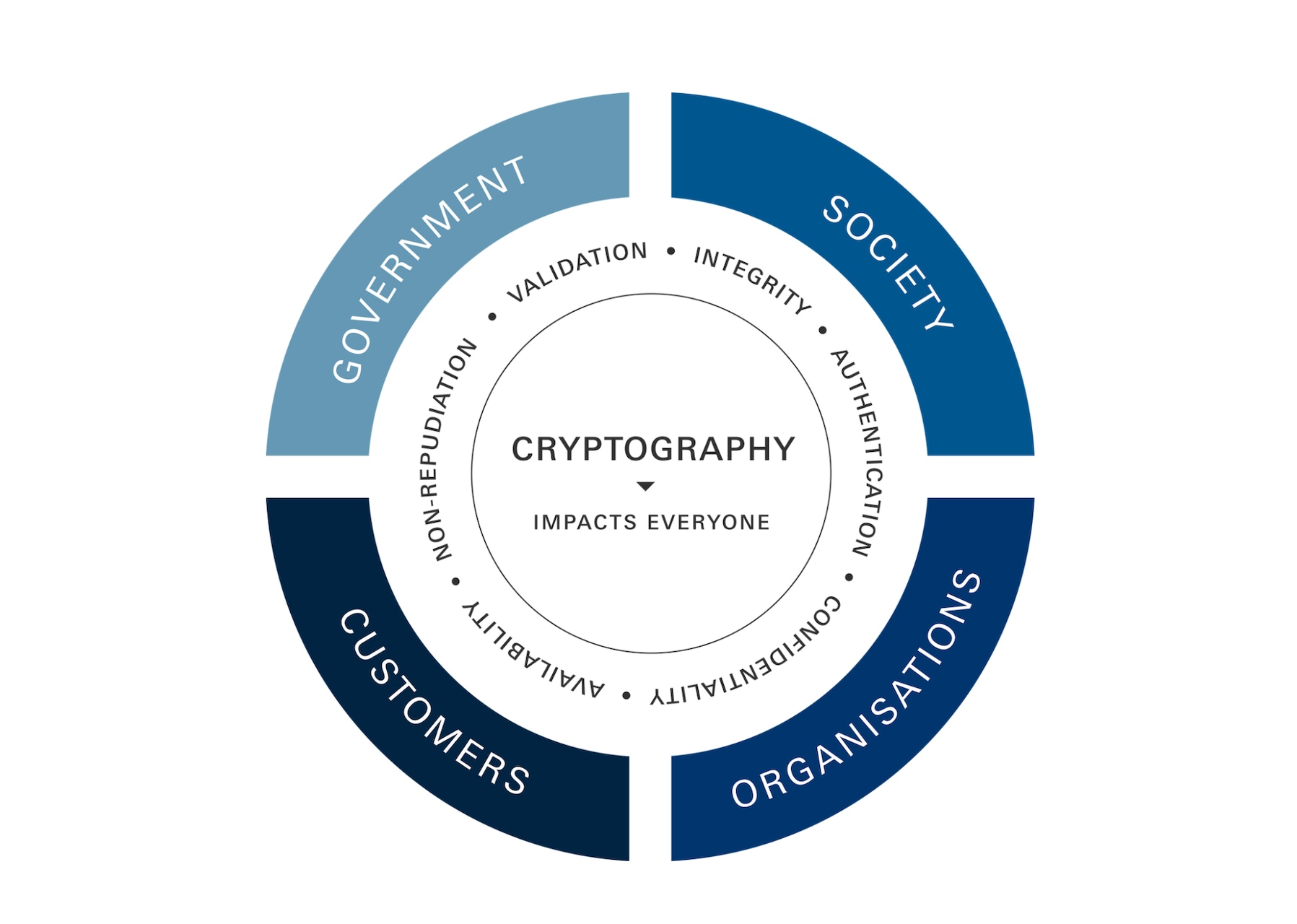
By the mid to late 2030s, quantum computers are predicted to have the potential to compromise today’s widely used encryption and authentication systems, specifically asymmetric cryptography based on public and private keys. Without the right and timely action, quantum computers could jeopardize digital security on a global scale.
Group of seven financial regulators are urging early action and government agencies, including those in the United Kingdom, Canada, United States and the European Union, are setting 2035 as the target year for a full migration to quantum safety and earlier deadlines, often by 2030, for more critical systems.
In each region, the day regulators make a formal request on the quantum preparedness of organizations for the first time, which we call “R-day,” marks a pivotal moment for regulated industries.
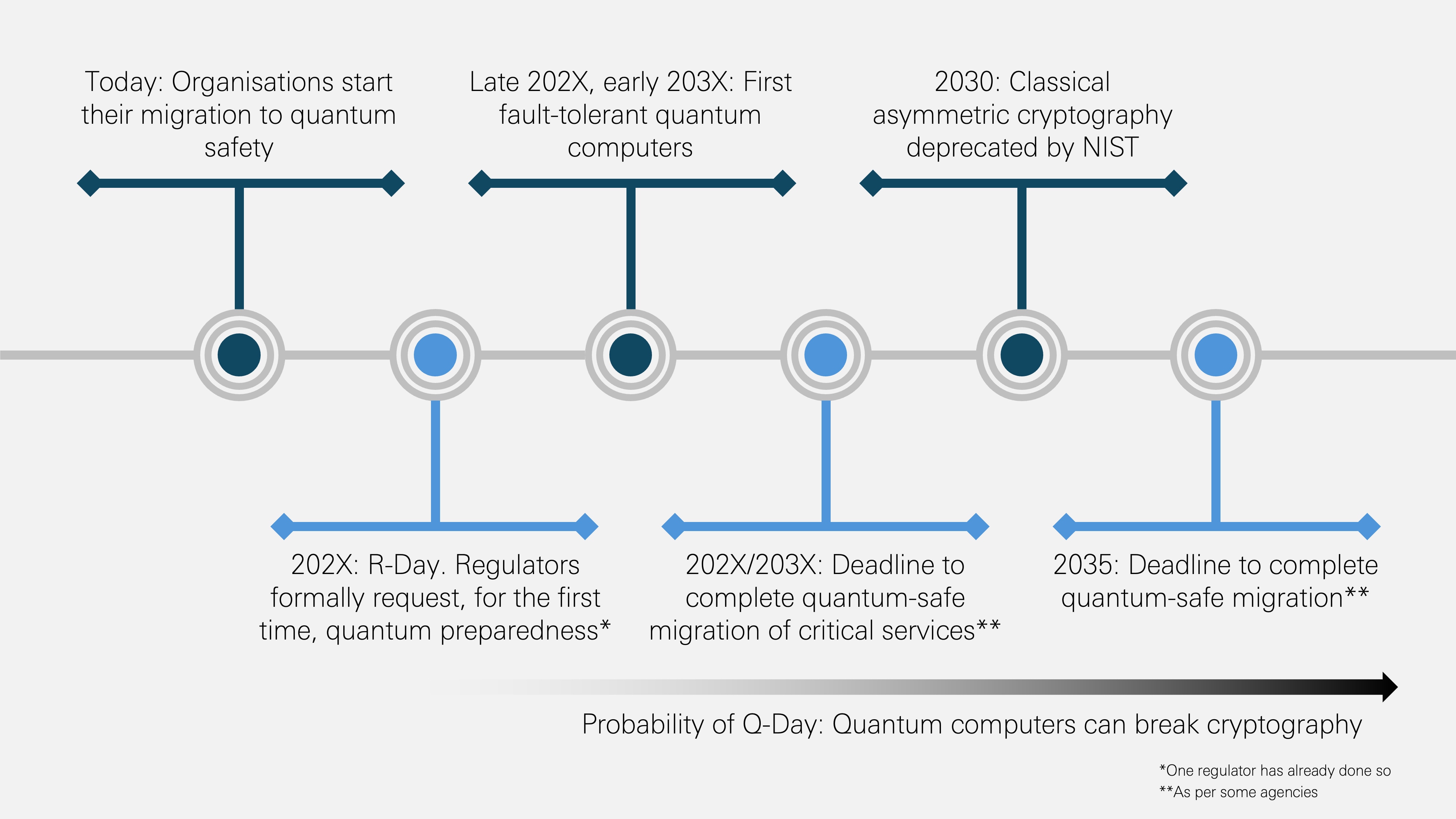
Here, we set out a new vision for quantum safety: that the quantum-safe migration is a unique opportunity for organizations to rethink and modernize their cybersecurity strategies, elevating cryptography as an asset that enhances business resilience.
Building a quantum-safe future
As technology advances, cybersecurity becomes more relevant. In this context, proactive cryptography management is essential to achieve resilient systems of the future. This contrasts with the traditional, reactive approach of many organizations to compliance requirements.
Three practices supporting a resilient cryptographic framework are cryptographic inventory, cryptographic agility and cryptographic defence-in-depth.

1. Cryptographic inventory
Building resilience starts with understanding an organization’s cryptographic landscape. Automating a complete inventory of cryptographic assets helps identify where they’re used, their properties and vulnerabilities, and how critical they are to the business.
This visibility delivers immediate benefits, such as spotting outdated or non-compliant assets, and over time can support operational efficiency by facilitating upgrades.
2. Cryptographic agility
Cryptographic agility is the ability to quickly update cryptography. This new approach to managing cryptography is becoming increasingly necessary in a world of fast-changing technologies, threats and standards. It can help lower long-term costs and enable quicker reaction times to emerging risks.
However, agility alone cannot fully mitigate certain threats, such as “store-now, decrypt-later” attacks identified by the G7 Cyber Expert Group or ringfence the effects of the sudden compromise of an algorithm. A comprehensive strategy pairs agility with complementary measures, such as defence-in-depth.
3. Cryptographic defence-in-depth
Cryptographic defence-in-depth leverages multiple layers of cryptography to mitigate the risk of relying on a single solution. By containing the impact of breaches, this approach helps ensure that critical systems remain secure even if one layer fails.
It also strengthens long-term resilience, preparing organizations for future technological shifts and enabling tailored solutions that meet diverse regulatory requirements and customer needs, such as long-term confidentiality.
Beyond security, cryptographic defence-in-depth fosters expertise, supports innovation and positions organizations to lead in an evolving regulatory and technological landscape.
Using diverse technologies is an approach that can already enhance resilience, enable differentiation and prepare organizations for when quantum computers can break cryptography.
”Technologies supporting cryptographic defence-in-depth
Each method used within a cryptographic defence-in-depth approach may leverage different trust assumptions. Organizations should choose technologies based on their risk appetite, resilience needs, regional best practices, regulatory obligations and desired level of simplicity, among other factors.
Post-quantum cryptography
Post-quantum cryptography (PQC) refers to public-key algorithms for key agreement and authentication designed to resist known quantum and classical attacks.
In 2024, the US National Institute of Standards and Technology (NIST) released the first PQC standards, which are expected to become a compliance requirement in many regions. Multinational organizations operating in these areas should prioritize NIST-approved PQC as the primary quantum-safe technology in their migration.
As these standards evolve, organizations can expect updates to best practices, guidelines and possibly regulations. Meanwhile, regions such as China and South Korea are developing their own PQC standards. To stay adaptable, cryptography strategies should be designed with flexibility to accommodate new technologies, regulatory divergence and emerging best practices.
In the short to medium term, a cryptographic defence-in-depth approach may combine PQC with existing, non-quantum-safe cryptography. Organizations with a longer-term outlook may also explore cryptographic defence-in-depth architectures that pair PQC with other quantum-safe techniques for certain use cases.
Key distribution centre technologies
Pre-shared keys and symmetric cryptography remain quantum-safe options for encrypting data in transit, at rest or in use. Manually distributing keys is still valuable for high-security scenarios but this approach is difficult to scale and poses logistical challenges.
Key distribution centre technologies use symmetric encryption to simplify key distribution and management in networks. However, they can create single points of failure that must be carefully mitigated to maintain resilience.
Today, these methods are mainly used in closed systems, such as the hardware layers of telecommunications networks, mobile phone authentication to carrier networks and securing internal access control systems.
Recent research and industry advances have produced new forms of “symmetric key infrastructure” such as quantum key distribution that address some of these concerns and expand potential use cases.
Quantum key distribution
Quantum communications enable a new approach to symmetric key exchange known as quantum key distribution (QKD). Unlike traditional methods, QKD’s security is rooted in quantum physics rather than assumptions about the difficulty of mathematical problems.
This means future advances in computing or mathematics cannot compromise its core security.
While QKD requires specialized hardware and is not a replacement for PQC, it can enhance resilience within a cryptographic defense-in-depth framework and support use cases demanding long-term confidentiality.
Seizing opportunities in the quantum-safe migration
As highlighted by the World Economic Forum’s Quantum Technologies: Key Strategies and Opportunities for Financial Services Leaders (2025), quantum technologies bring unprecedented opportunities. The migration to quantum safety is no exception: it is a challenge but also an opportunity.
Early adoption can strengthen an organization’s leadership, trust posture and client confidence. Increasingly, organizations expect their partners to include quantum-safe migration plans within their technology roadmaps as a condition for maintaining long-term relationships.
The shift also opens doors to innovation through advanced classical cryptographic techniques, such as fully homomorphic encryption and multi-party computation, as well as quantum cryptography.
A well-designed and measured migration plan is necessary and will provide reassurance to customers and regulators. Through greater knowledge of an organization’s cryptography posture, it can also help remediate existing, yet unidentified cryptography risks.
Using diverse technologies is an approach that can already enhance resilience, enable differentiation and prepare organizations for when quantum computers can break cryptography. However, such an evolution will take time. Given its scale, it is prudent to integrate this approach to resilience into the general strategy for quantum safety at its onset.
To thrive amid uncertainty, organizations should proactively harness emerging technologies, make informed choices and manage cryptography with long-term resilience and risk management in mind.
We would like to thank Philip Intallura and Will Collison for their contribution and fruitful discussions.
Don't miss any update on this topic
Create a free account and access your personalized content collection with our latest publications and analyses.
License and Republishing
World Economic Forum articles may be republished in accordance with the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License, and in accordance with our Terms of Use.
The views expressed in this article are those of the author alone and not the World Economic Forum.
Stay up to date:
Cybersecurity
Related topics:
Forum Stories newsletter
Bringing you weekly curated insights and analysis on the global issues that matter.
More on CybersecuritySee all
Vince Tizzio and Lori Bailey
January 19, 2026






