The 4 profiles of cyber-resilient organizations: which colour are you?

True cyber resilience requires a blend of approaches. Image: Getty Images
- Cyber resilience isn’t a one-size-fits-all fixed model; it’s a practical, evolving journey shaped by context.
- Resilient organizations blend profiles, rather than fit neatly into one type as conditions change.
- Knowing your profile sharpens leadership decisions; to guide strategy, understand leadership fit and find capability gaps for what’s next.
Cyber resilience is a practice, not a theory. There is no single resilience-building plan that fits all organizations and their circumstances because each one has a specific individual risk profile, governance and culture of work, among other contextual factors. The path to resilience is not the same for any two organizations.
Yet some common traits and characteristics are emerging. In response to the constraints that organizations have in common – such as regulations, incidents and market dynamics – they are taking similar views of what “good” resilience journeys look like and are therefore leveraging similar approaches to improve cyber resilience.
It’s rare for an organization to follow one single profile; cyber resilience often requires a blend, with an emphasis in one or two areas. There is no good or bad profile, only different approaches, which suit the context.
By consciously understanding the organization’s profile(s), leaders can understand how their organization is positioned today to evaluate and strategize for tomorrow: whether this resilient profile is right for what’s coming, if your leadership style suits the organizational profile you're working in, and what skills gaps you might need to close to leverage a different approach to cyber resilience.
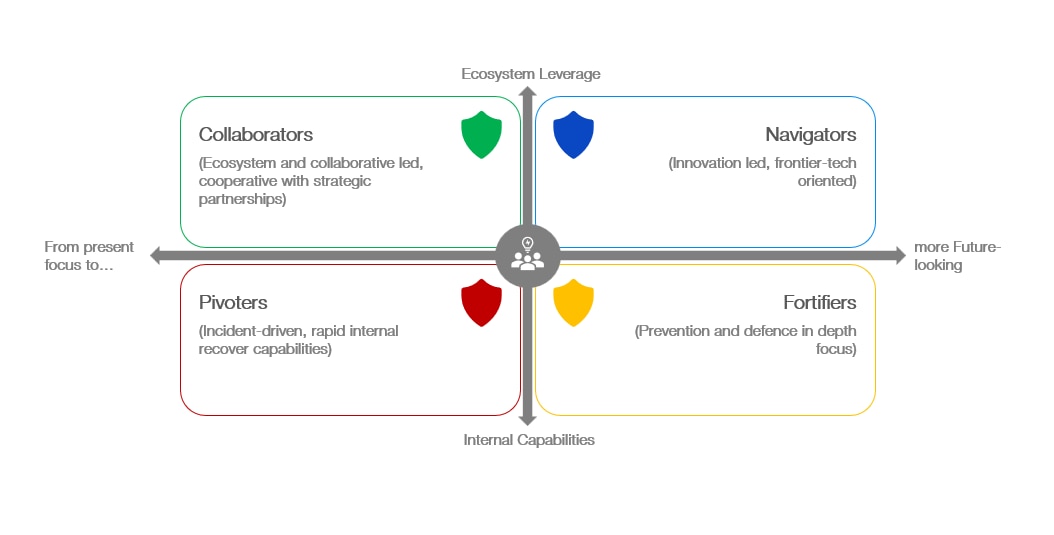
Four profiles of cyber-resilient organizations
- Red: the Pivoters: traits include being agile, responsive, and focused on quick recovery during cyber incidents. Context-wise, this is common after an incident, with a focus on improving agility, response methods and times, based on a recent incident experience.
- Yellow: the Fortifiers: traits include being proactive, heavily defended, and invested in robust preventative measures. Context-wise, this is common before a cyber incident or during “peacetime,” to strengthen defences in anticipation of existing and emerging cyberthreats.
- Green: the Collaborators: traits include being community-driven, cooperative, and focused on shared intelligence/partnerships and supply chain. Context-wise, this is commonly a response adopted to ecosystem change, such as a shift in external dynamics, suppliers, or mergers and acquisitions.
- Blue: the Navigators: traits include being forward-thinking, innovative, always planning for emerging threats. Context-wise, this is common after a market change, such as new regulation, a business opportunity or in a growth market. This can be where resources are plentiful, or where constraints have stimulated innovation.
If they all sound good, that is because they are. Each profile has its own strengths and weaknesses, which are driven and merited by different contexts. Let’s dig deeper.
Red: the Pivoters
Red organizations are not static. They characteristically have strong and swift incident response capabilities, with an emphasis on the ability to respond to threats. Red organizations have effective disaster recovery plans and can rapidly contain threats.
Red organizations are usually working with resource pressures like a tight budget and small teams, and must prioritize speed and growth over extensive cybersecurity practices. This profile is often seen in startups and smaller businesses, who can be crucial parts of the supply chain, and in industries with tight profit margins.
This pivoter mindset can result in lacking proactive defences, not developing adequate prevention methods and an over-reliance on reactive measures. Quick response is not a substitute for long-term strategic planning and investment.
If you are in a Red organization, here are some hallmark characteristics that you might recognize:
- Red organizations need adaptive and responsive leadership. A CISO with a sense of urgency and a background in incident management is often appreciated by the teams they are leading in this context. Just after an incident is not the time to reflect deeply on long-term strategies, but strategic CISOs bring a strength that could help organizational resilience for the long-term.
- Crisis management is strong, as this is often called upon and a common measure for the performance of the security function.
- Technical systems will often support, or hinder, robust response, so these often receive investment and prioritization by crisis management teams.
- On the people and culture side, burn-out and hero culture in teams can be the downfall for Red organizations. Resilience is a marathon, not a sprint, and Red organizations cannot – and should not – stay in firefighting mode forever.
Blue: the Fortifiers
Blue organizations are heavily defended. They have characteristically invested in robust preventative measures to prevent incidents before they happen. Blue organizations typically have traits like strong perimeter defences, layered security architectures and well-established compliance processes.
This approach can result in strength, but also ossification at the cost of flexibility. Hence, Blue organizations may face more challenges to adapt their internal processes and infrastructure to novel threats, with high maintenance costs.
Blue organizations are usually working to fortify in strict regulatory environments and risk-averse contexts, driven by their privileged position – either holding high-value data or imperative for customer trust. This profile is often seen in organizations with legacy technology and a long history, such as financial institutions, healthcare providers and well-funded government bodies.
If you’re a Blue organization, here are some hallmark characteristics that you might recognize:
- Blue organizations value reflective and long-term strategic leadership. A CISO with multi-year tenure and a background in risk management is often appreciated by the teams they are leading in this context. However, a CISO with a dynamic approach and agile response brings a strength that could help the organizational resilience for the long-term.
- GRC (governance, risk management and compliance) is strong, as this is embedded in the organization’s DNA and is often a measure for the performance of the security function.
- Technical systems are robust and auditable, to allow for adequate compliance and confidence.
- Business processes are the historical foundation on how the organization works, but ossification is a common pitfall. Revisiting and modernizing business processes can ensure they are still as fit for purpose today (and for the future) as when they were designed.
Green: the Collaborators
Green organizations are connected. These characteristically cooperative organizations are focused on sharing intelligence, strengthening partnerships, and building security into their supply chain. Green organizations build partnerships and communities, and their connectedness can level up the ecosystem, through fostering public-private partnerships.
This collaboration and connectivity approach brings additional exposure linked to the ecosystem volatility and dependency on partners. There are communication challenges in coordinating across many stakeholders, and third-party organizations bring their own portfolio of risk.
Green organizations are usually operating in a connected ecosystem, with shared dependencies and a need to multiply defender effort, based on their tight budgets. These traits are often seen in global organizations that have disproportionate effects on our physical environments, those with a large supply chain such as manufacturing, and critical infrastructure.
If you’re a Green organization, here are some hallmark characteristics that you might recognize:
- Green organizations value visible leadership that can build communities inside and outside the organization. A CISO with a strong network and public profile is often appreciated by the teams they are leading in this context. However, an inward-looking CISO could strengthen internal organizational links to build organizational resilience for the long-term.
- Ecosystem management is a critical component of how the organization manages its exposure and benefits from the community defender effort.
- Business processes are developed in partnership – with both upstream and downstream organizations, to avoid bottlenecks and unknown dependencies.
- GRC is crucial but can be under-resourced. As connectivity and complexity grows, so should the funding and effort to manage risk – and regulation initiatives are stepping up for this sector.
Yellow: the Navigators
Yellow organizations focus on innovation and planning for emerging threats, so these profiles are characteristically the first to invest in advanced technologies and focus on long-term strategies, changing the way the entire ecosystem approaches resilience. With a tech-first approach, the legacy dependency is low, and zero-trust is non-negotiable.
This pioneering approach can bring challenges to balance innovation with real ROI. Using untested approaches can set a new paradigm, or end in spectacular failure.
Yellow organizations often have large budgets and dedicated R&D teams, driven by a need to maintain a competitive edge or lead in the cybersecurity industry due to market demands. This profile is often seen in larger organizations in technology or cybersecurity, or in innovative industries with valuable IP.
If you’re in a Yellow organization, here are some hallmark characteristics that you might recognize:
- Yellow organizations value innovative and bold leadership. A CISO who is comfortable with a blank canvas in dynamic circumstances, and who wants to lead in the industry, is often a good match for context. However, a CISO with solid grounding in the basics, and tried-and-tested methods, can also be a healthy challenge and a strength that could help the organizational resilience for the long-term.
- People and culture are strong, as technical foundations will never be valuable without the right culture – having people, belief and the right attitude aligned behind the initiative is crucial.
- Yellow organizations recognize their disproportionately powerful role in the ecosystem – they can set paradigms and really shift the needle, making their contributions to initiatives and public-private partnerships all the more valuable.
- Crisis management maintains their strong brand reputation, but overconfidence can be Yellow’s undoing. A small or medium incident that a Yellow organization handles with ease would be a career-defining incident for most other organizations – but that means when a large crisis hits, a Yellow organization can be blindsided, and the potential knock-on effects are wide-ranging and global.
What organization are you?
Cyber resilience journeys differ among organizations. There is no right or wrong, just different approaches to ensure that the organization’s primary goals and objectives are delivered. Each profile places emphasis in different areas of the Cyber Resilience Compass: technical systems, crisis management, people and culture, business processes, ecosystem, leadership and GRC.
Cyber resilience is not about choosing the “right” model, but about ensuring the organization’s resilience is appropriate for its operating context, to guide strategy, adapt leadership styles, and find capability gaps to prioritize.
Global organizations have different contexts and industries, requiring tailored actions. The most resilient organizations are dynamic and consciously adapt, combining strengths from different profiles over time to sustain trust, continuity and long-term value. A lack of awareness of different profiles can result in frustration; for example, an approach that worked very well at a Red organization can bring difficulties or resistance at a Yellow organization.
Knowing the cyber resilience profile of an organization can remove friction when searching for cultural fit in leadership, ultimately helping to recruit for, or adapt to, the appropriate leadership style. This knowledge also guides strategy, understanding where an organization has historically invested in security, and why – and therefore where it should broaden and diversify its approach. Understanding the profile of an organization can identify potential friction points, i.e. the areas in which another otherwise appropriate approach to building cyber resilience would clash or jar with an opposing profile.
No matter the context, here are five actions to take this from theory to practice:
- Assess your current cyber resilience profile.
- Adapt the leadership approach in harmony with the organizational profile.
- Align and prioritize the areas of the Cyber Resilience Compass that are important for that profile.
- Continue to implement capability-building programmes that align to the organizational needs.
- Through training and awareness programmes, build a culture aligned with the cyber resilience profile.
Don't miss any update on this topic
Create a free account and access your personalized content collection with our latest publications and analyses.
License and Republishing
World Economic Forum articles may be republished in accordance with the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License, and in accordance with our Terms of Use.
The views expressed in this article are those of the author alone and not the World Economic Forum.
Stay up to date:
Cybersecurity
Forum Stories newsletter
Bringing you weekly curated insights and analysis on the global issues that matter.
More on CybersecuritySee all
Alejandro R.-P. Montblanch, Leon Molchanovsky and Michele Mosca
January 26, 2026






