How cybersecurity can best navigate geopolitics to secure a resilient and open digital future

Cybersecurity is now intertwined with geopolitics Image: Getty Images/iStockphoto
- Cybersecurity has moved from a technical concern to a core element of geopolitical competition, shaping how states, companies and societies manage risk and power.
- Sovereignty-driven regulations and export controls are fragmenting the digital landscape and raising risks for organizations operating across borders.
- Building cyber resilience now depends on collaboration between business and government, as geopolitical shocks and hybrid threats expose deep interdependencies in the digital ecosystem.
The world is entering a new phase of geopolitical competition. Intensifying rivalries between major powers, coupled with rapid technological change, are reshaping how nations, companies and societies operate. In this environment, cybersecurity has moved far beyond a technical concern confined to IT departments. It has become a strategic issue at the heart of international relations, business resilience and public trust. Against this backdrop, the Global Cybersecurity Outlook 2026 finds that 91% of the largest organizations (those with more than 100,000 employees) have changed their cybersecurity strategies in response to geopolitical volatility.
Three forces stand out: the deepening connection between cybersecurity and geopolitics, the challenges of sovereignty and regulation and the urgent need for resilience.
How is cybersecurity impacted by geopolitics?
Cyber operations have become core instruments of statecraft, used for espionage, sabotage, signalling and influence. This shift means that every organization and especially every Chief Information Security Officer, is effectively a geopolitical actor.
The shifting balance of global power and the emergence of a more multipolar international system are challenging established norms and weakening long-standing multilateral institutions. At the same time, middle powers and unconventional actors including, but not limited to, hacktivists and organized crime networks, gain influence. This creates a more unpredictable threat landscape where attribution is difficult and hybrid attacks blur the lines between state and non-state activity.
Concurrently, governments in many parts of the world are asserting greater control over cyberspace. This includes stricter data localization rules, increased surveillance and efforts to shape how technology companies manage information. For the private sector, this raises complex questions: should organizations comply with government demands for access or prioritize protecting individual rights and embedding principles such as 'do no harm' in their operations?
How does sovereignty challenge cybersecurity?
One of the most disruptive forces in cybersecurity today is the surge in sovereignty-driven regulations. From data localization requirements to mandatory vulnerability disclosures, governments are asserting greater control over digital domains. Yet, these rules diverge across jurisdictions, creating a complex patchwork of compliance that adds operational friction and strategic risk for multinational companies. These sovereignty-driven shifts are also changing how organizations assess and prioritize cyber risk.
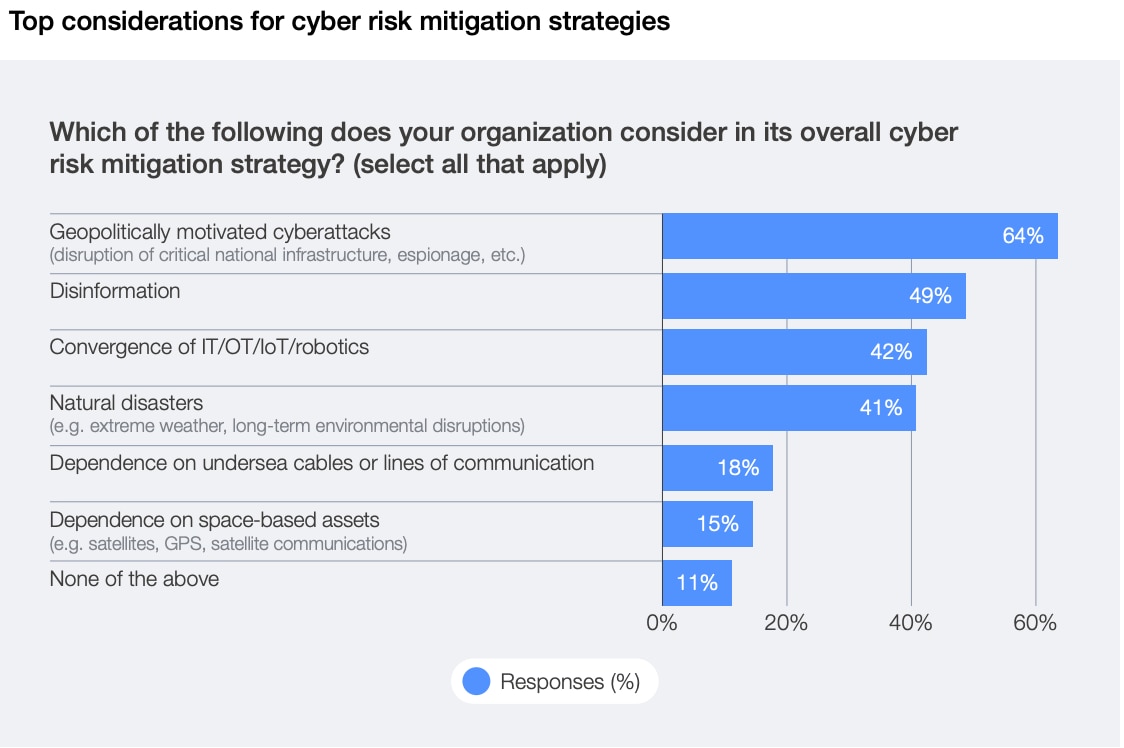
The Global Cybersecurity Outlook 2026 finds that some 64% of organizations are accounting for geopolitically motivated cyberattacks – such as disruption of critical infrastructure or espionage – in their overall cyber risk mitigation strategy.
At the same time, export controls on advanced technologies – including semiconductors, artificial intelligence and quantum technologies – are also fragmenting the global innovation landscape. These restrictions are spurring the development of separate ecosystems, raising the prospect of a divided digital world where technology standards diverge along geopolitical lines.
In response, organizations are adapting by building federated security models, maintaining regionalized stacks and diversifying supply chains. Yet, these measures come with trade-offs, including higher costs and, in some cases, reduced resilience.
How can we build resilience through collaboration?
Concentration risk and supply chain dependencies are emerging as some of the most pressing risks in this fragmented environment. The growing reliance on a handful of technology providers means that geopolitical shocks, such as sudden restrictions or sanctions, could trigger cascading operational disruptions across sectors and borders. Hybrid warfare, which fuses cyberattacks with physical and information operations, further complicates the picture, as evidenced by recent incidents targeting Europe’s critical infrastructure. These dynamics reveal the deep interdependence of the digital ecosystem - where instability in one area can quickly cascade across the rest.
To counter these risks, several strategies are gaining traction:
- Diversification through on-premises or multi-cloud solutions to avoid single points of failure.
- Zero-trust approaches to account for shifting alliances and blurred distinctions between friends and adversaries.
- Proactive planning, including playbooks for escalation and de-escalation during geopolitical crises.
- Closer collaboration with national security agencies to improve preparedness and crisis management.
What happens in cyberspace no longer stays in cyberspace
Cybersecurity leaders increasingly recognize that organizations cannot afford to be reactive. The pace of geopolitical change is too fast and the stakes are too high. Companies must anticipate fragmentation, invest in resilience and recognize that in today’s world, their decisions carry geopolitical weight.
What happens in cyberspace no longer stays in cyberspace. It shapes economies, democracies and the global balance of power. The challenge ahead is to ensure that businesses and governments work together to secure a digital future that is resilient and open.
Don't miss any update on this topic
Create a free account and access your personalized content collection with our latest publications and analyses.
License and Republishing
World Economic Forum articles may be republished in accordance with the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License, and in accordance with our Terms of Use.
The views expressed in this article are those of the author alone and not the World Economic Forum.
Stay up to date:
Cybersecurity
Forum Stories newsletter
Bringing you weekly curated insights and analysis on the global issues that matter.
More on CybersecuritySee all
Sander Zeijlemaker and Michael Siegel
February 4, 2026